Single sign-on with Entra prerequisites
- Ambassador Cloud Enterprise Subscription.
- Cloud Application Administrator access to the Entra admin center for your organization.
- Your unique case sensitive company ID provided by Ambassador Support.
Step 1: Create an Entra application
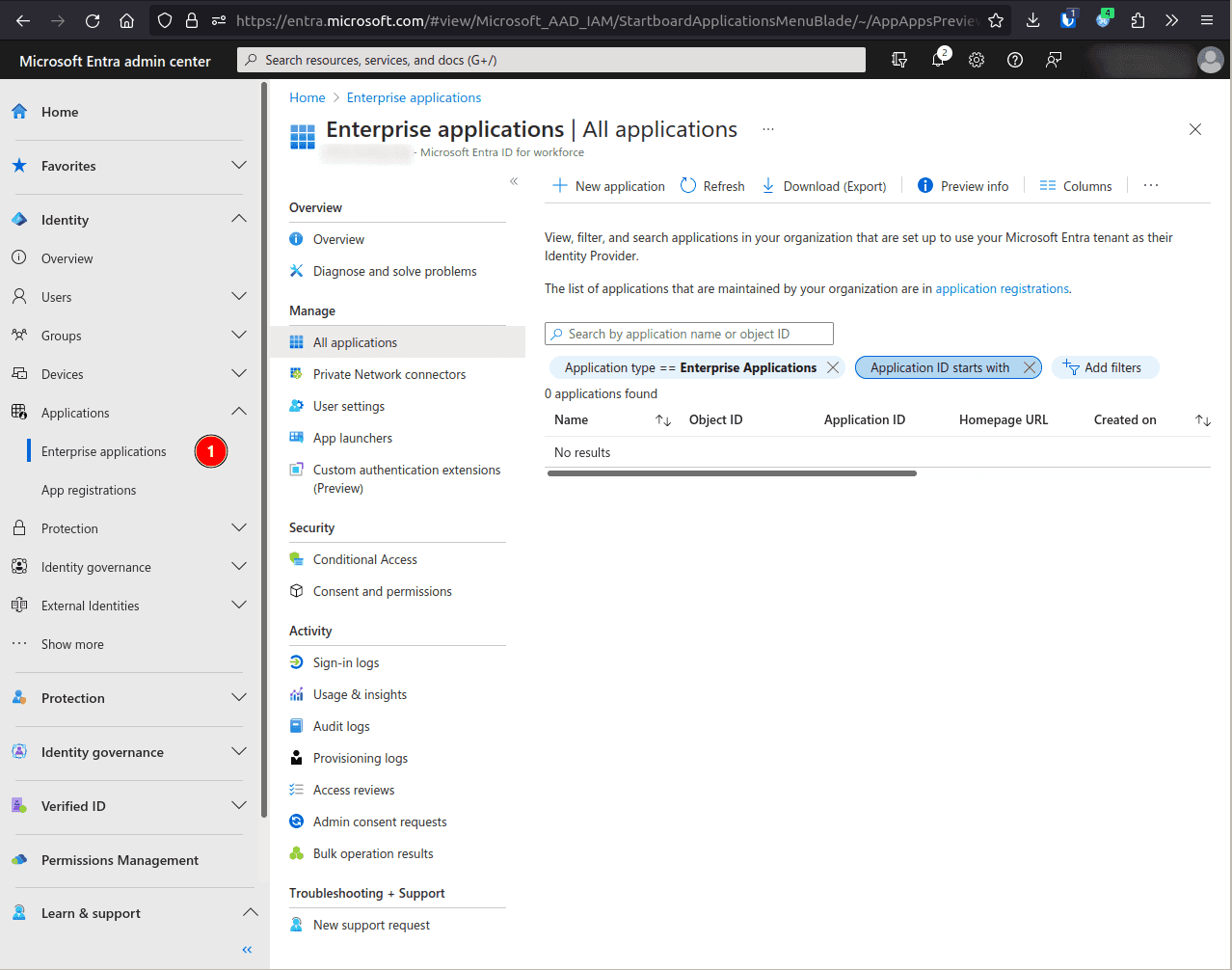
Go to the Entra Admin console for your company.
Browse to Identity > Applications > Enterprise applications.
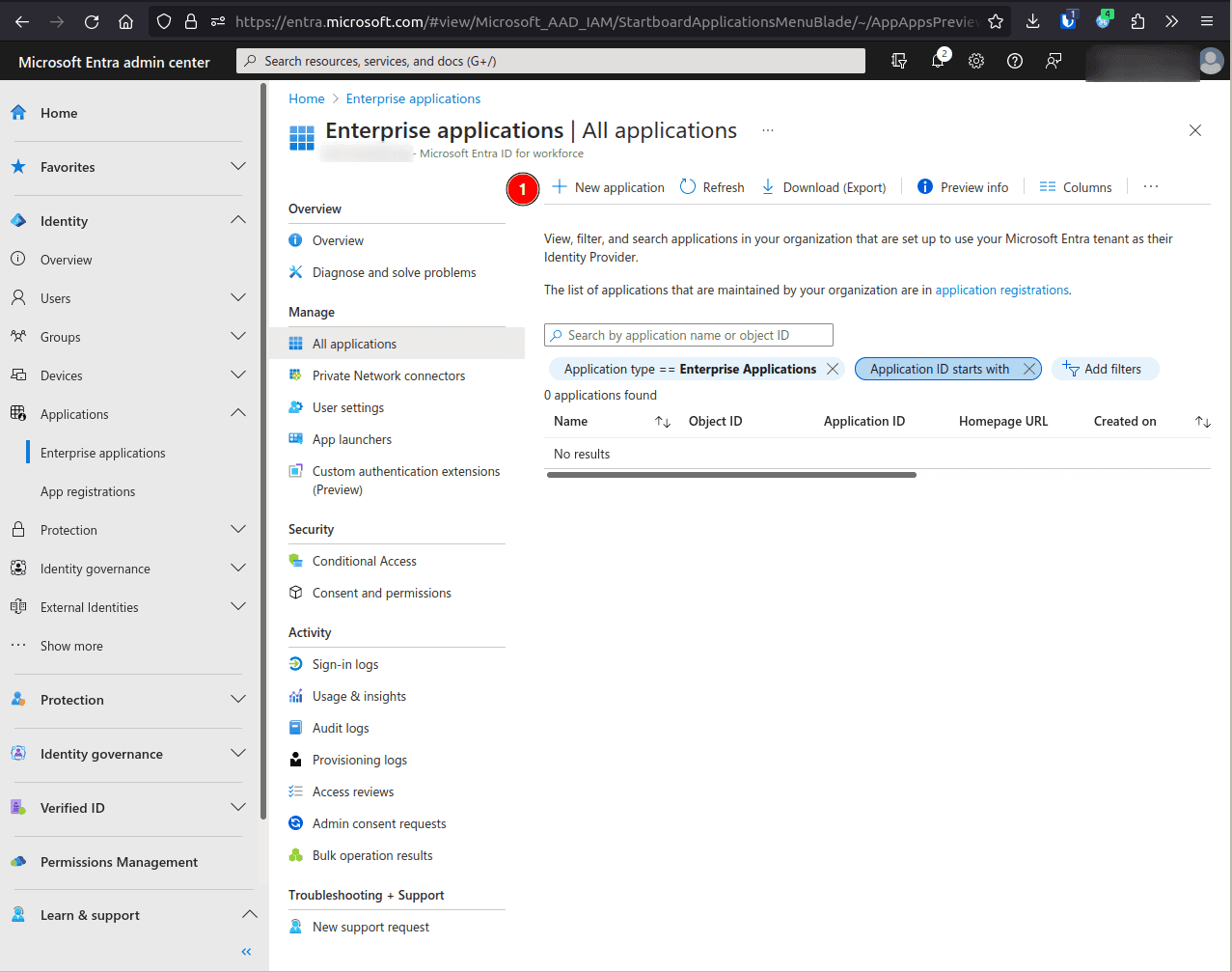
Select New application.
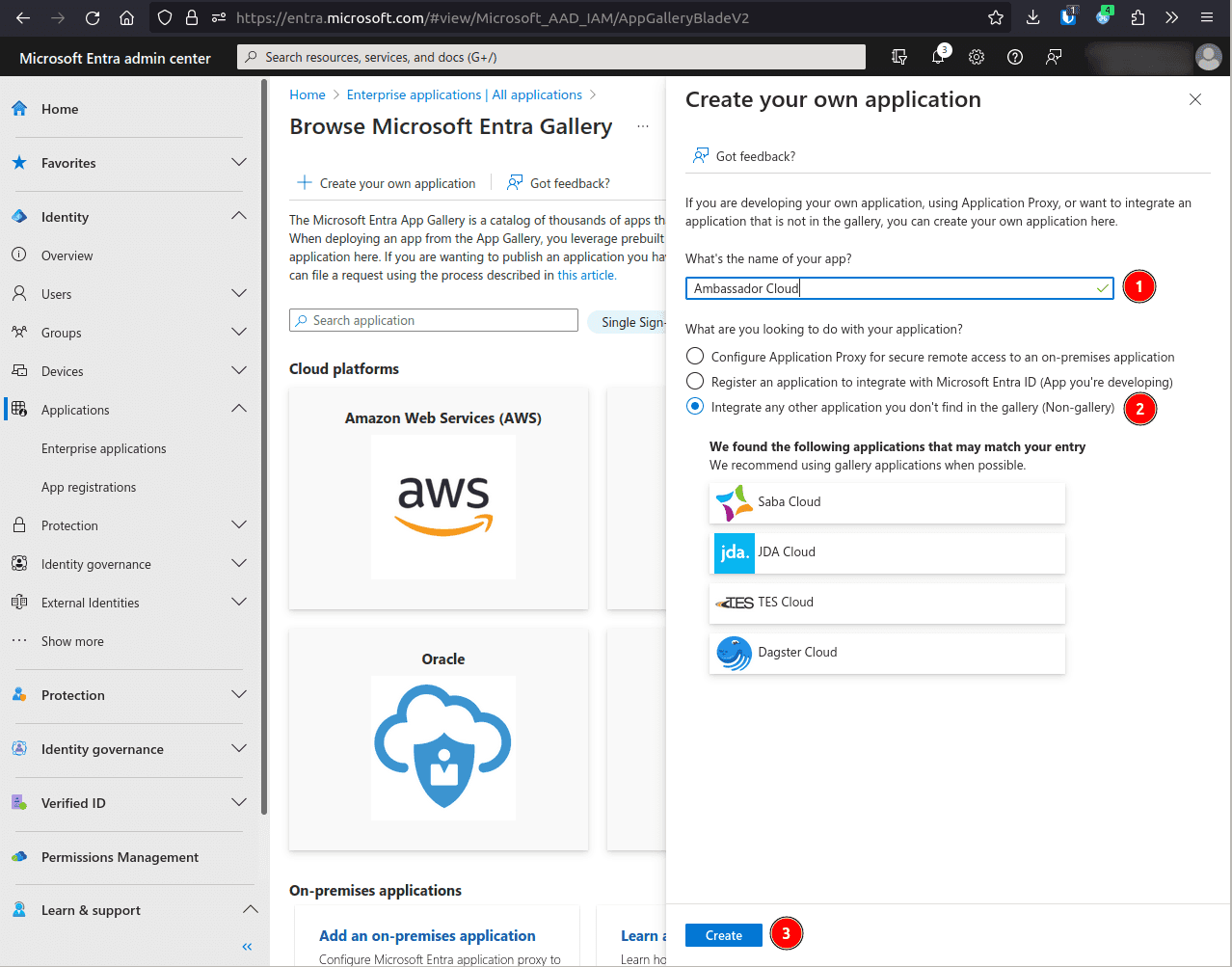
Select Create your own application.
Enter Ambassador Cloud as the app name, select option Integrate any other application you don't find in the gallery (Non-gallery) and click Create.
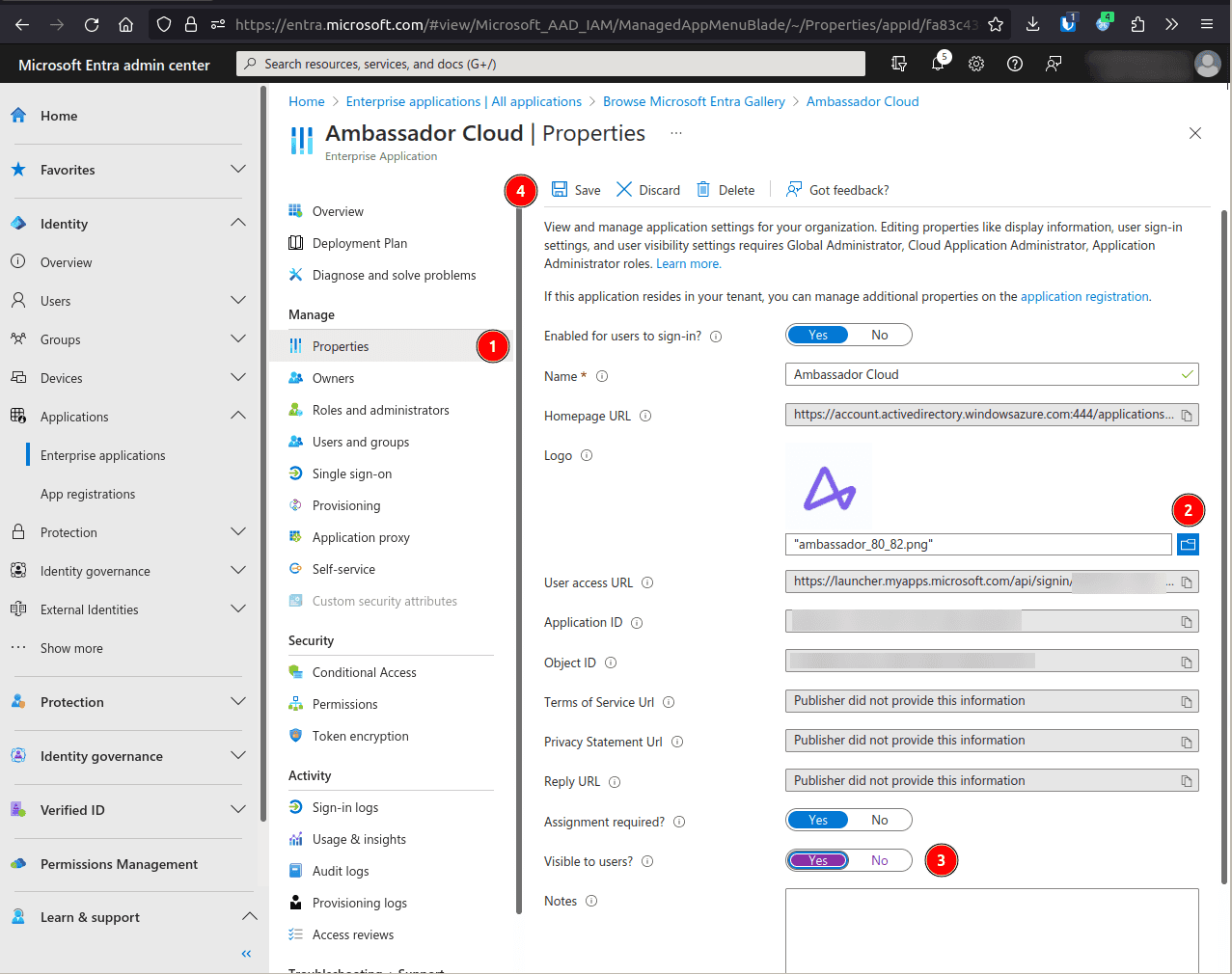
On the application page, select Properties, and upload the Ambassador Logo. Set the Visible to users? option to
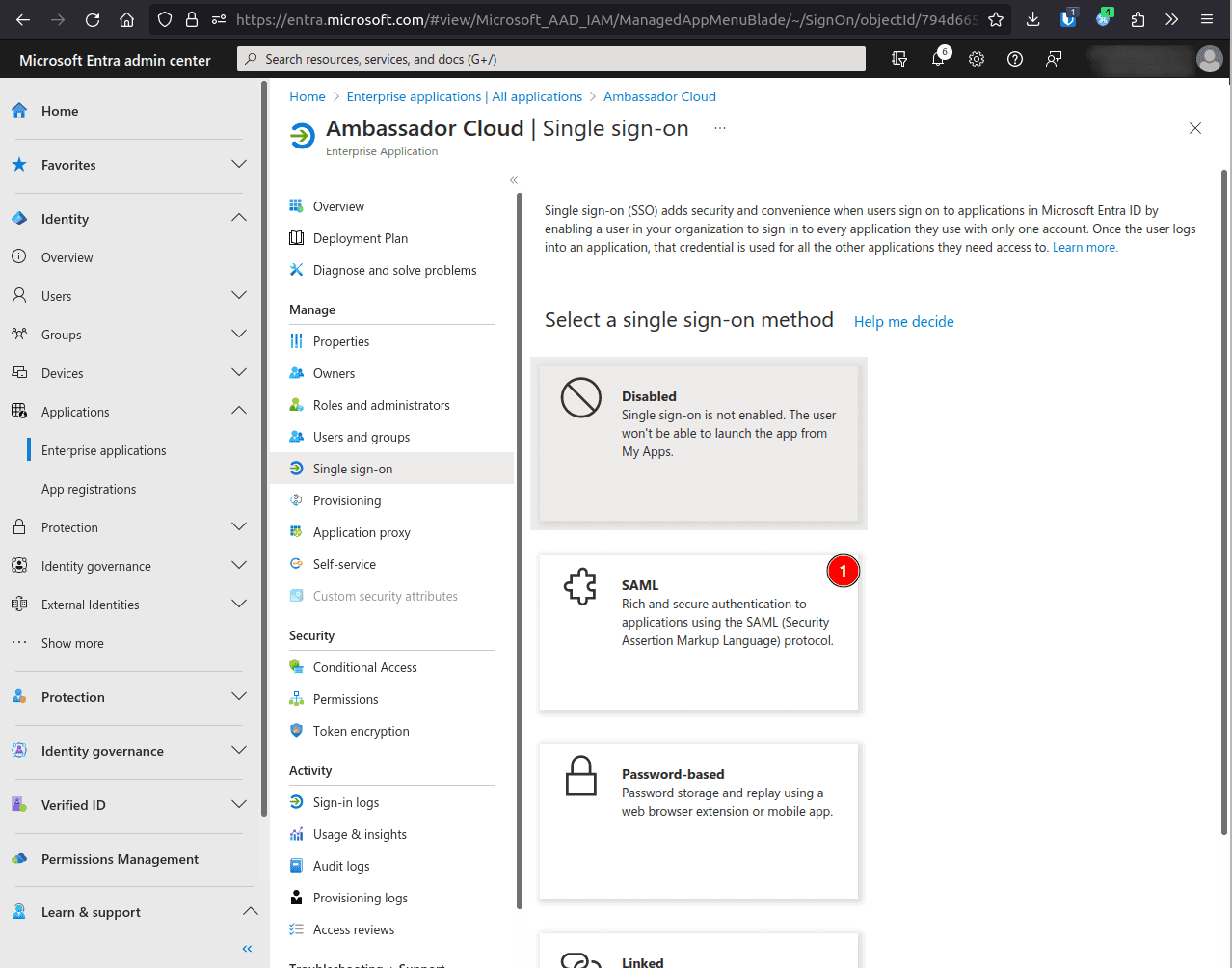
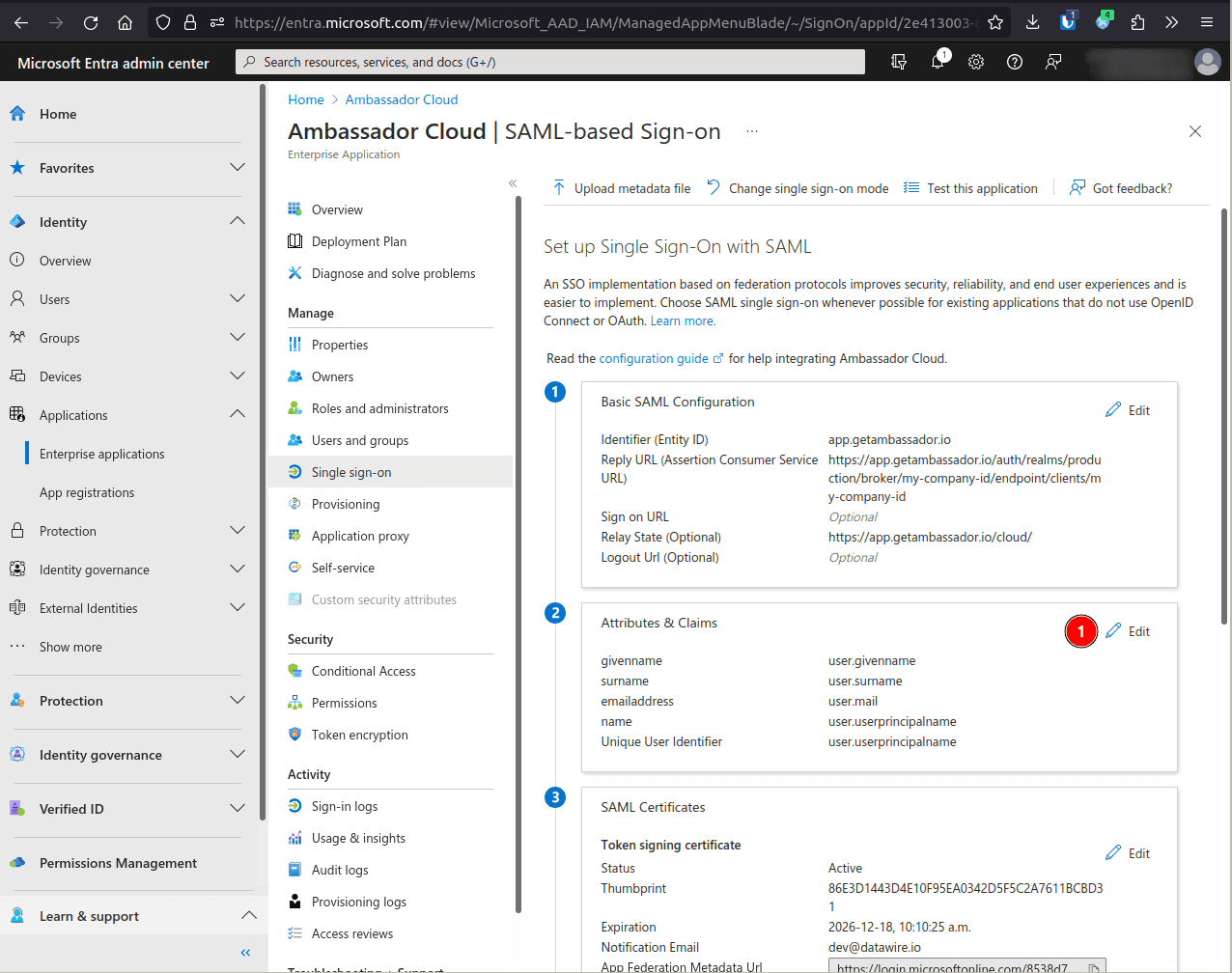
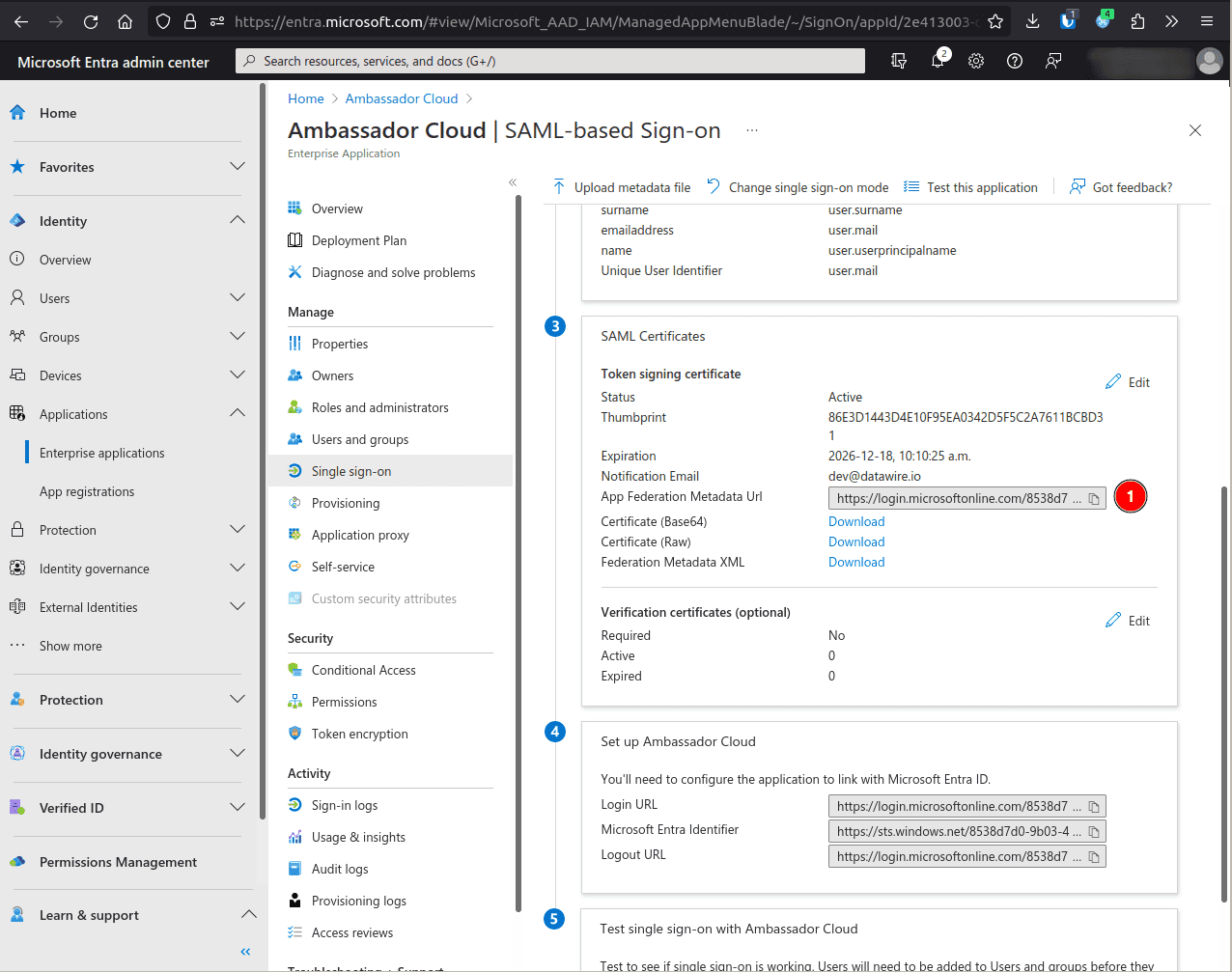
Yesand hit Save.On the application's page, Single sign-on, and select SAML as the sign-on method.
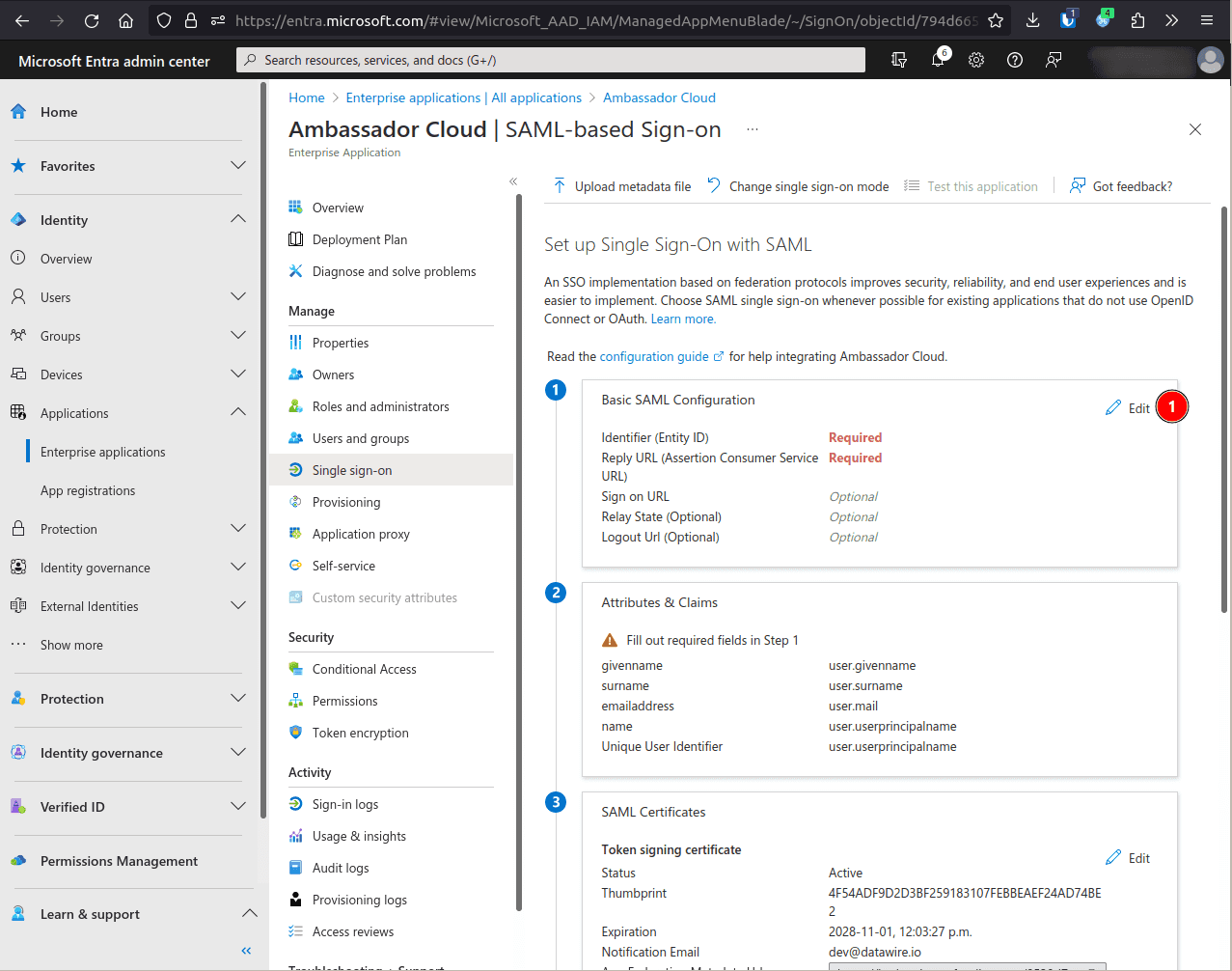
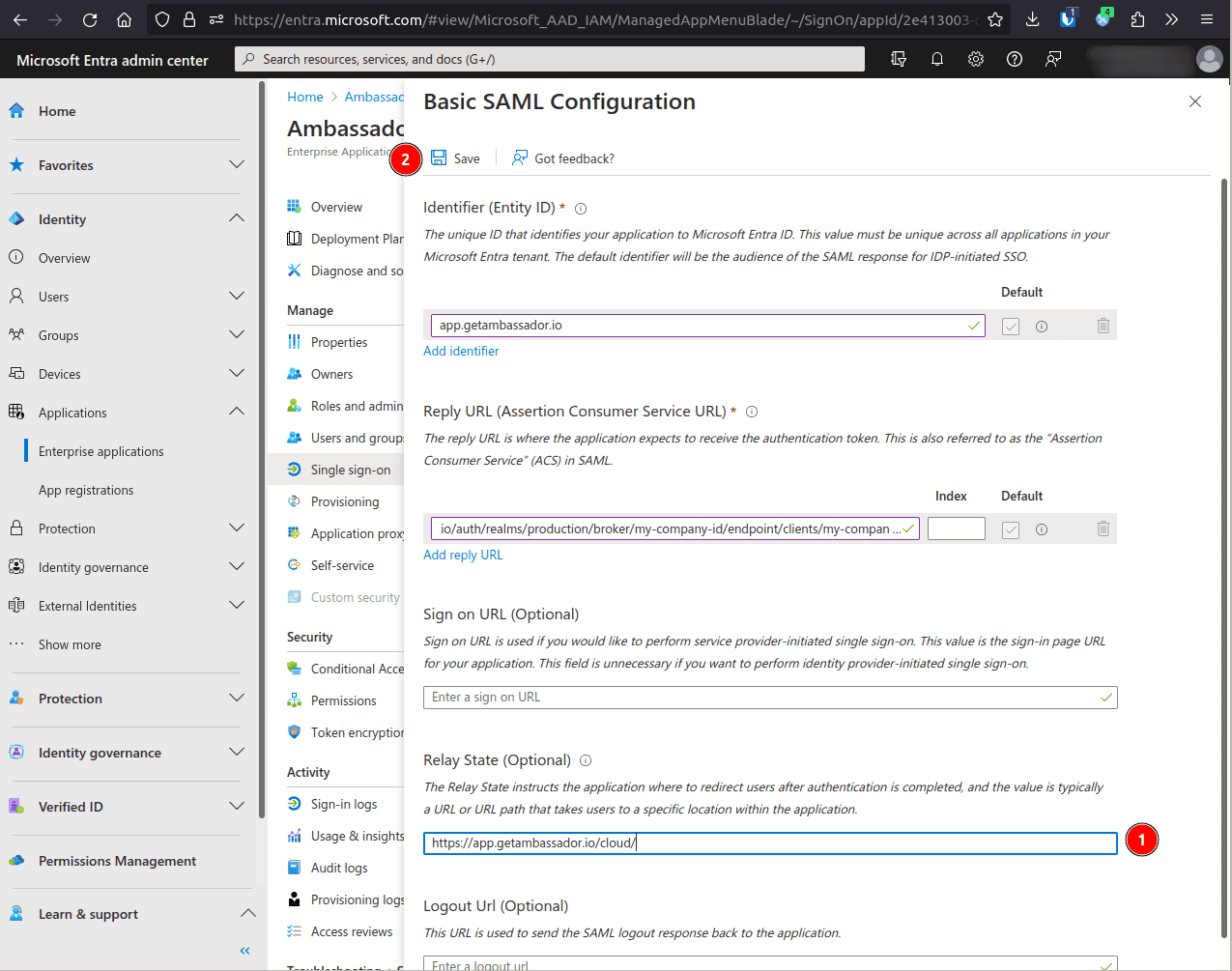
Edit the Basic SAML Configuration
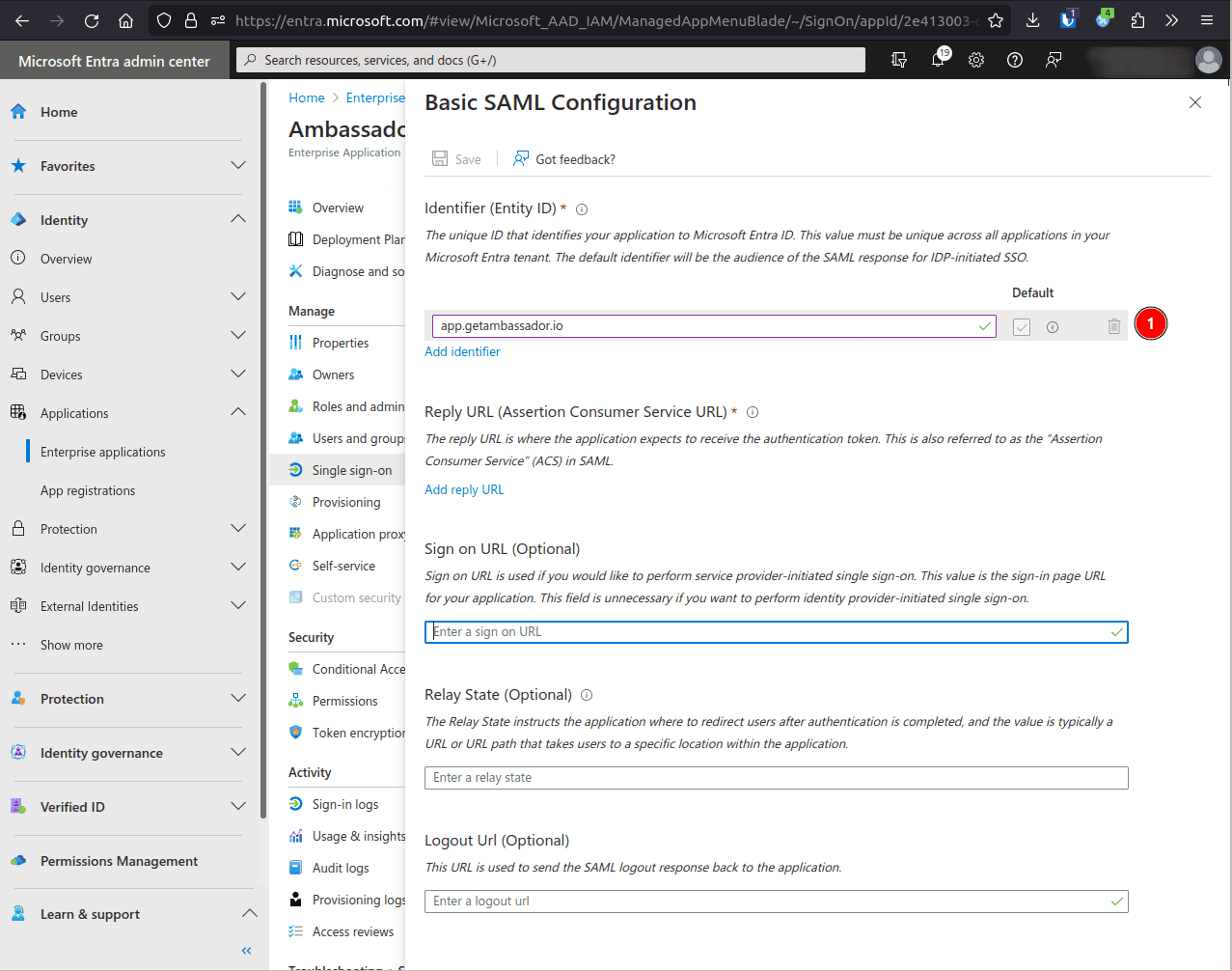
In the Identifier (Entity ID) field, click Add identifier and enter app.getambassador.io.
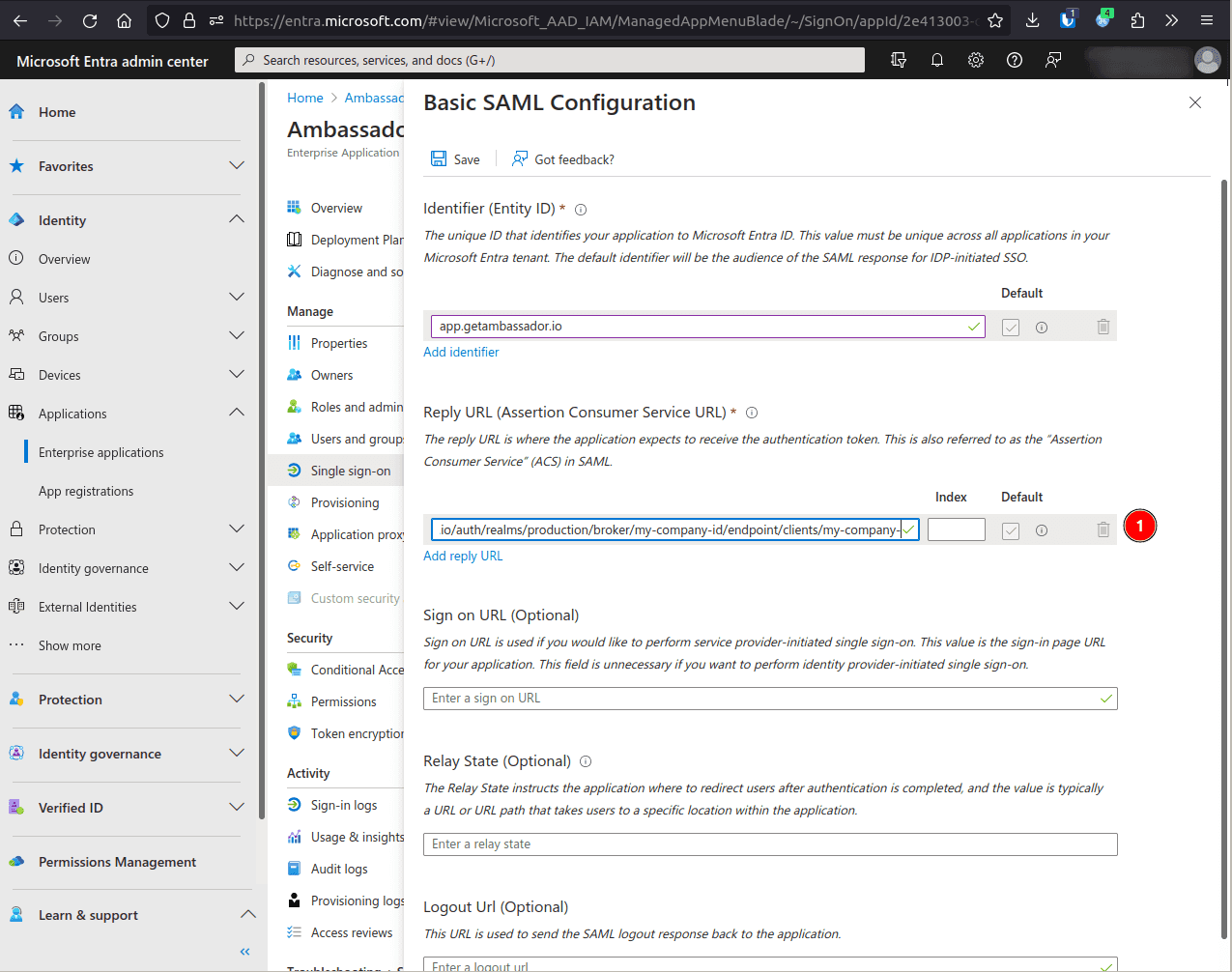
- Enter your case sensitive company ID here and then copy this URL to use in the next step:https://app.getambassador.io/auth/realms/production/broker/<company-id>/endpoint/clients/<company-id>
In the Reply URL (Assertion Consumer Service URL) field, click Add identifier and enter the above URL (after inputting your case-sensitive company ID).
In the Relay State (Optional) field, enter https://app.getambassador.io/cloud/ and click Save.
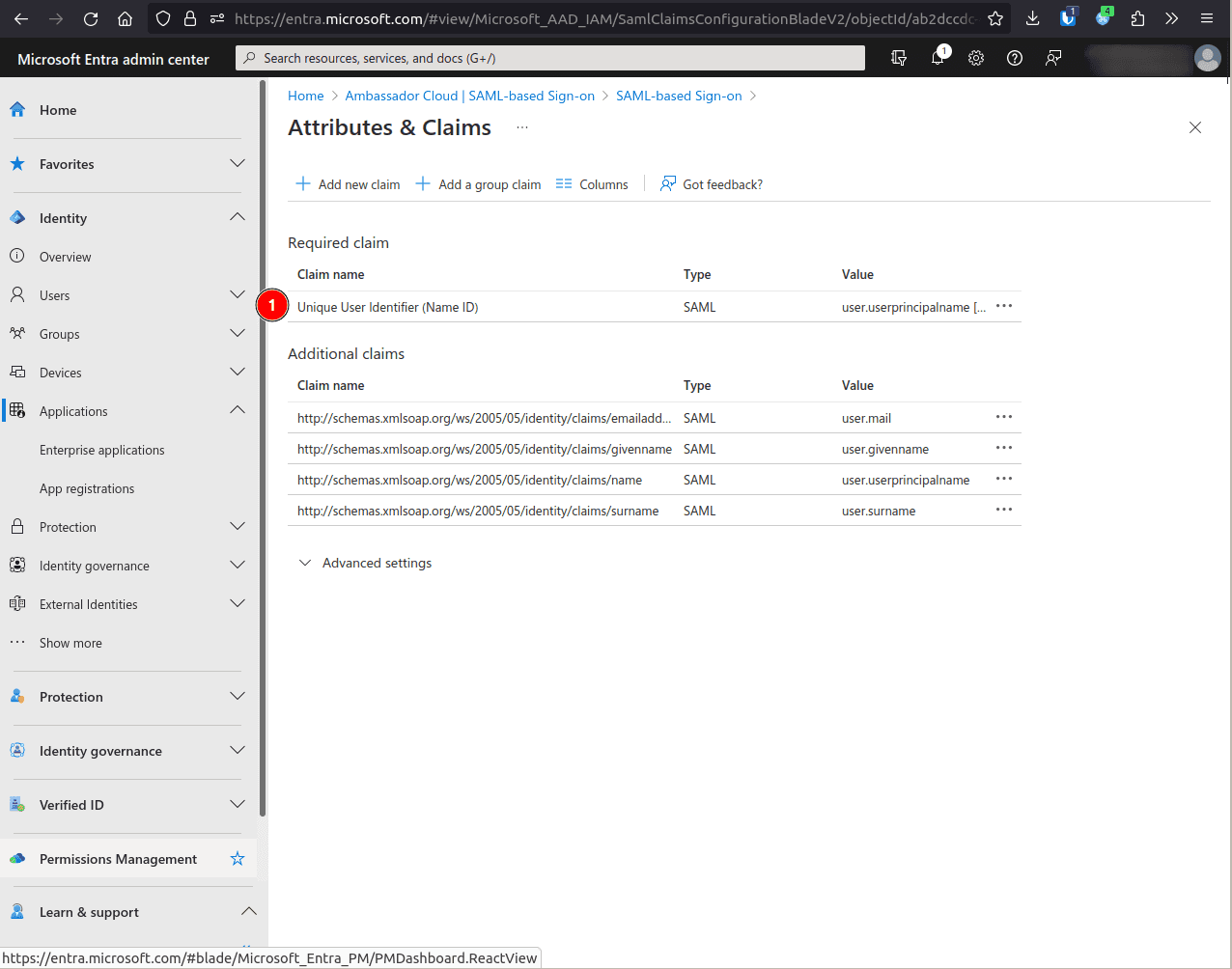
Edit the Attributes & Claims.
CLick the Unique User Identifier (Name ID) claim.
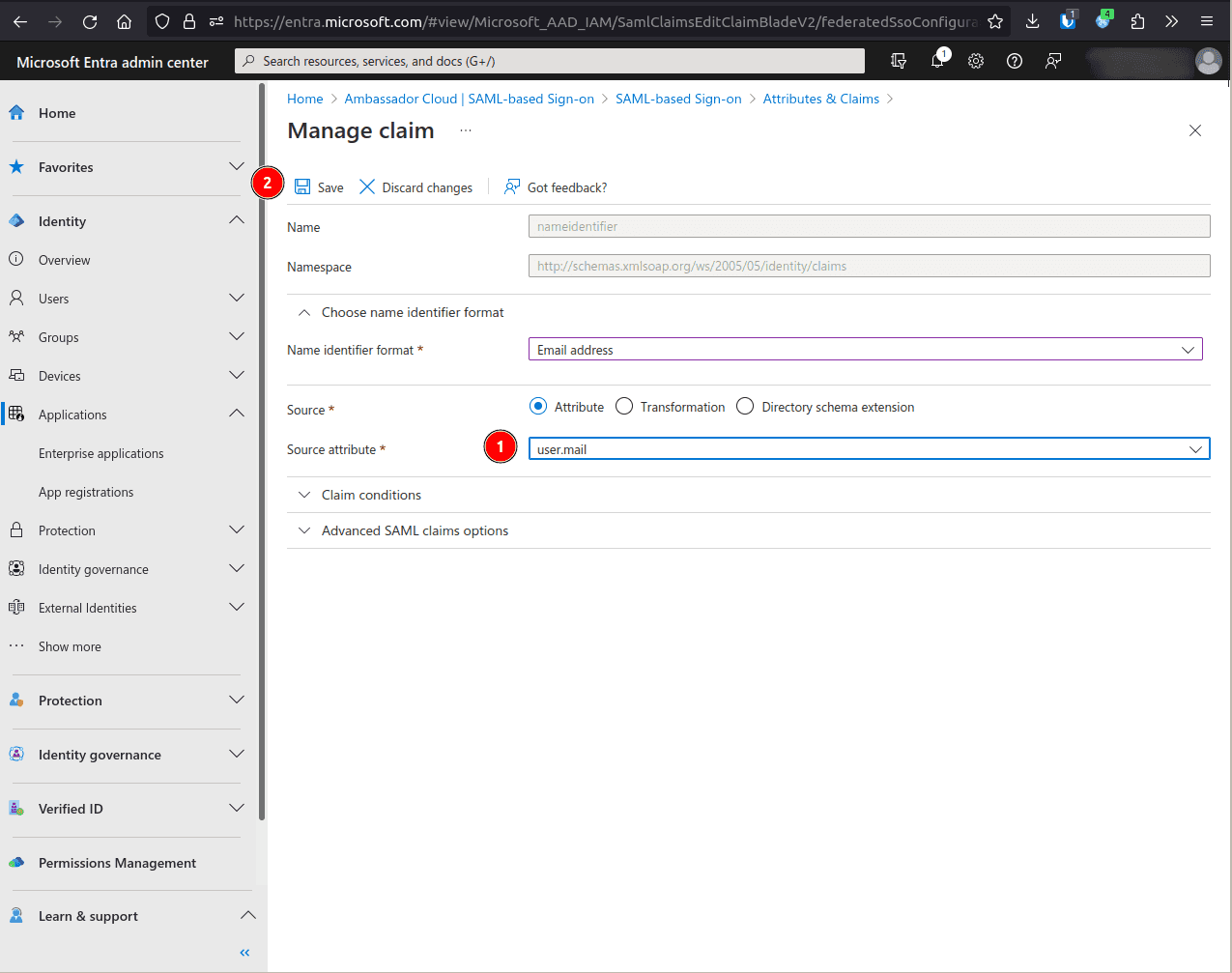
In Source attribute select
user.mailand Save.Back on the Signe sign-on screen, copy the App Federation Metadata Url value and give it to support to complete the configuration.
When your Application is created you should be able to see it in the MyApps portal.
Step 2: Assign your application to people or groups
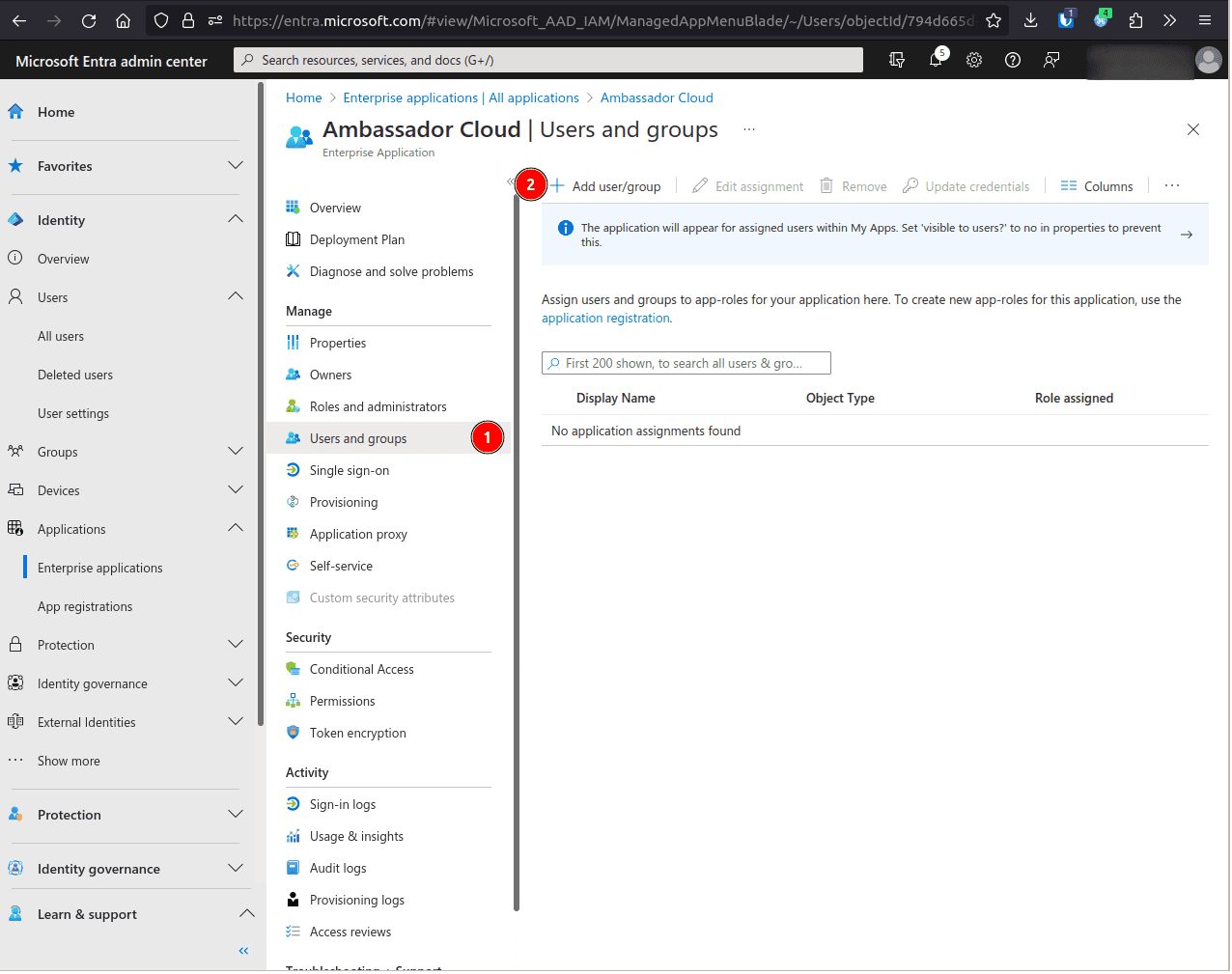
Go to Identity > Applications > Enterprise applications and select the Ambassador Cloud application.
Select Users and groups and click Add user/group
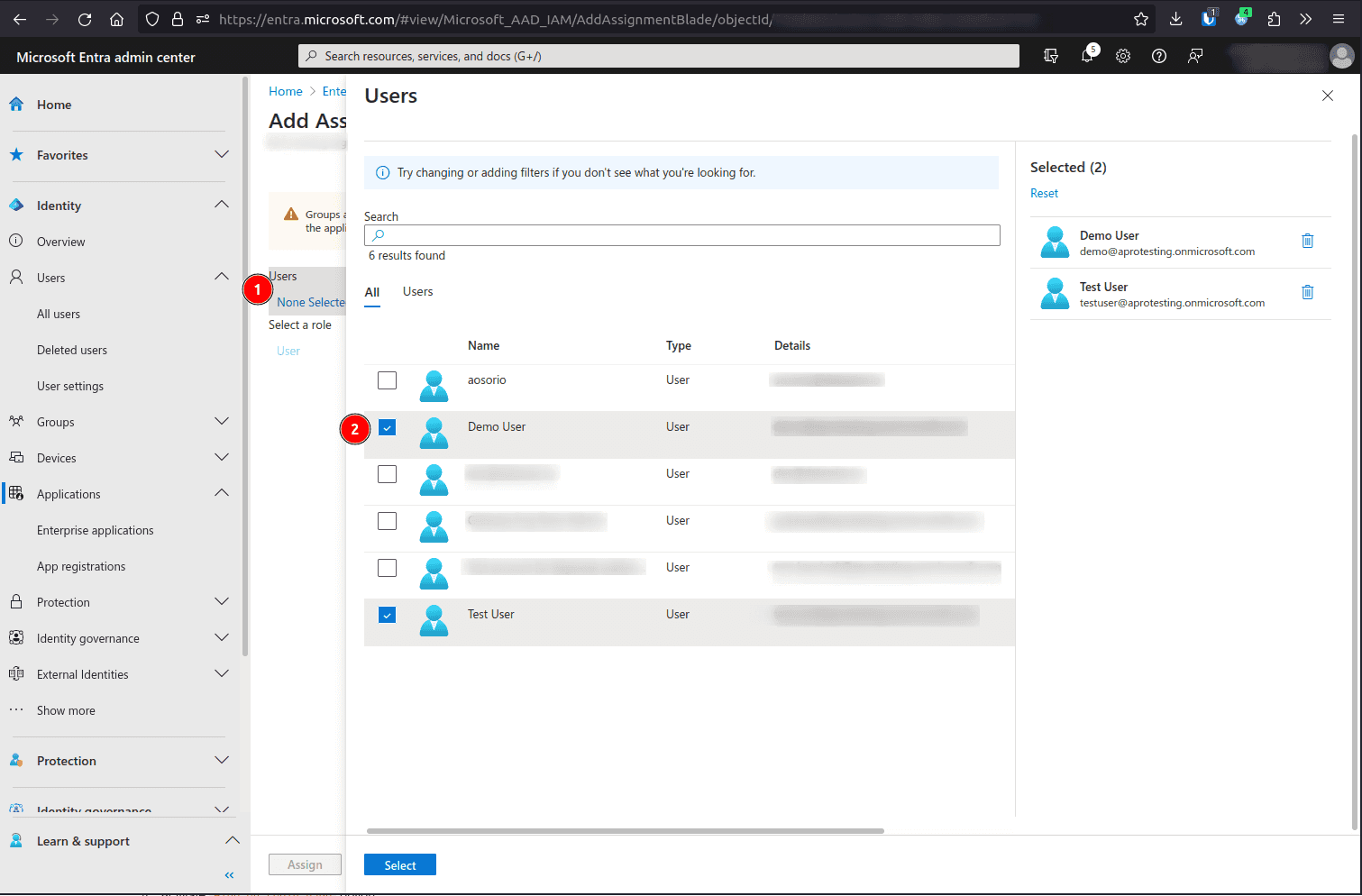
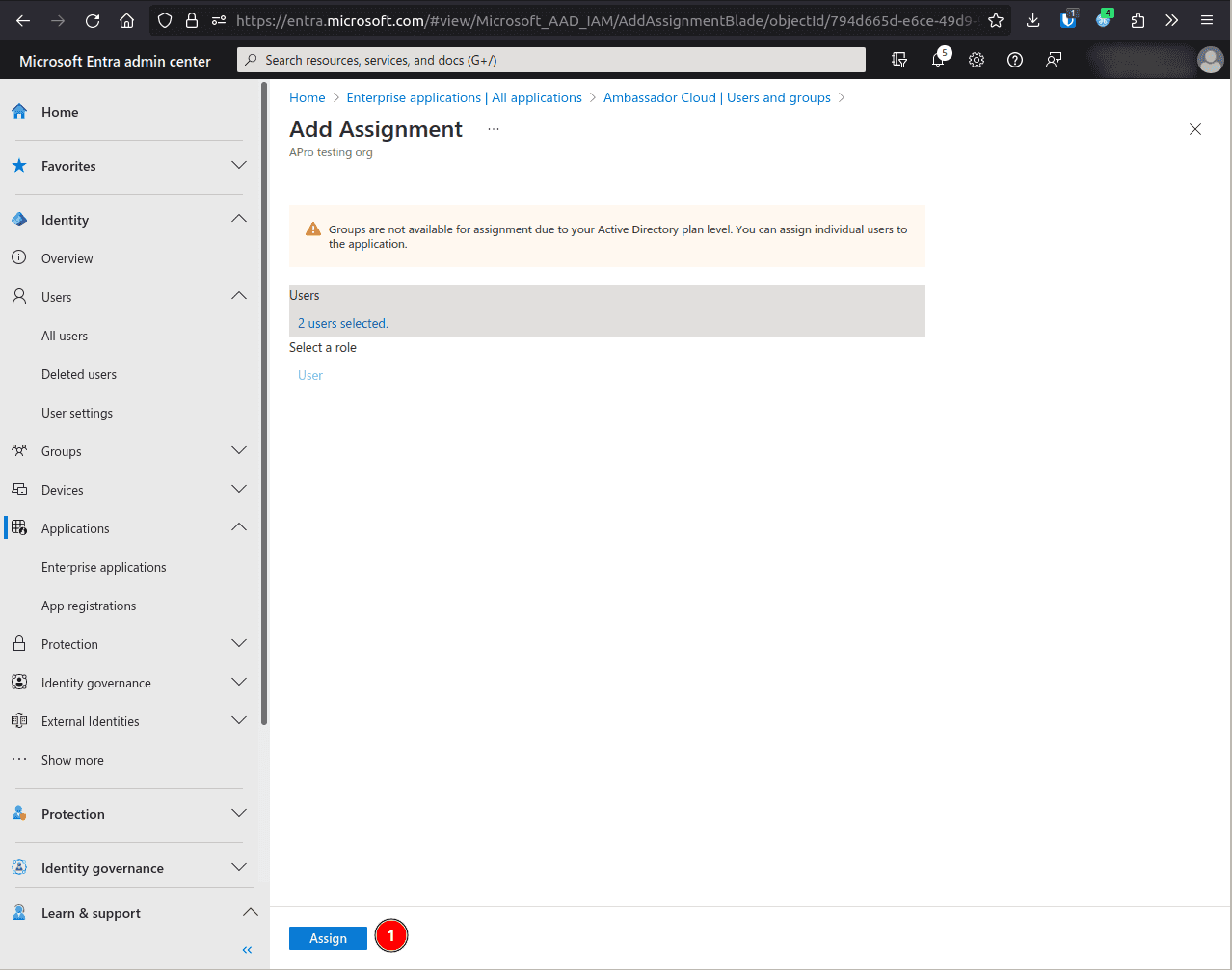
Under the Users section, assign as many users/groups as required.
Save your changes.
Go to the application properties and make sure that the option Assignment required? is set to
Yes.
Step 3: Test your application integration
Once your support contact has notified you that your SSO integration has been activated, you will want to test it to ensure that it is working properly. If these tests do not proceed as expected, then please schedule a live debug session with your Ambassador Support contact.
To test Identity Provider initiated Sign On, you should ensure that you are starting from a logged out browser with clean state by creating a new incognito session for each test.
Go to MyApps portal.
You should see the Ambassador Cloud application on your dashboard. If you do not then make sure your user is added to the Application as described in Step 2
Click on the Ambassador Cloud application. You should end up at the Ambassador Cloud website and be logged in.