DocsEdge Stack
Ambassador Edge Stack quick start
Ambassador Edge Stack quick start
Contents
1. Installation
Getting a license from Ambassador Cloud
We'll start by installing Ambassador Edge Stack into your cluster.
Ambassador Edge Stack requires a license to function, so the first step is getting one to use while installing. If you are in air-gapped environment, please contact sales.
Log in to Ambassador Cloud with GitHub, GitLab or Google and select your team account.
Provide a name to identify your Kubernetes cluster and then press Generate Key
Copy the token and follow along here.
Once your cluster is connected to Ambassador Cloud, a community license is automatically applied.
We recommend using Helm to install but there are other options below to choose from.
2. Routing traffic from the edge
Ambassador Edge Stack uses Kubernetes Custom Resource Definitions (CRDs) to declaratively define its desired state. The workflow you are going to build uses a simple demo app, a Listener CRD, and a Mapping CRD. The Listener CRD tells Ambassador Edge Stack what port to listen on, and the Mapping CRD tells Ambassador Edge Stack how to route incoming requests by host and URL path from the edge of your cluster to Kubernetes services.
Start by creating a
Listenerresource for HTTP on port 8080:Apply the YAML for the "Quote" service.
Generate the YAML for a
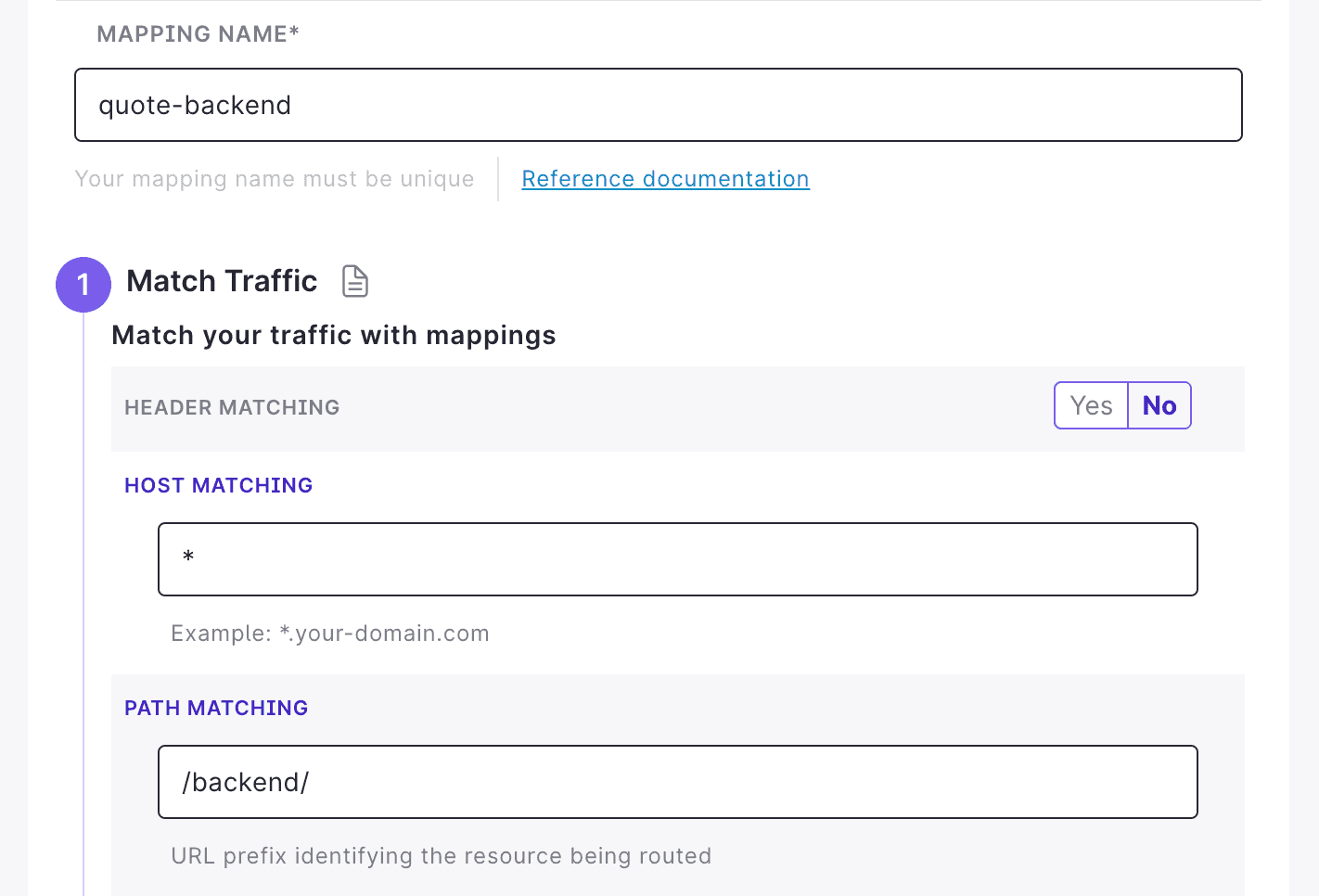
Mappingto tell Ambassador Edge Stack to route all traffic inbound to the/backend/path to thequoteService.In this step, we'll be using the Mapping Editor, which you can find in the service details view of your Ambassador Cloud connected installation. Open your browser to https://app.getambassador.io/cloud/services/quote/details and click on New Mapping.
Default options are automatically populated. Enable and configure the following settings, then click Generate Mapping:
Whether you decide to automatically push the change to Git for this newly create Mapping resource or not, the resulting Mapping should be similar to the example below.
Apply this YAML to your target cluster now.
Store the Ambassador Edge Stack load balancer IP address to a local environment variable. You will use this variable to test access to your service.
Test the configuration by accessing the service through the Ambassador Edge Stack load balancer:
 What's next?
What's next?
Explore some of the popular tutorials on Ambassador Edge Stack:
- Intro to Mappings: declaratively routes traffic from the edge of your cluster to a Kubernetes service
- Host resource: configure a hostname and TLS options for your ingress.
- Rate Limiting: create policies to control sustained traffic loads
Ambassador Edge Stack has a comprehensive range of features to support the requirements of any edge microservice.
To learn more about how Ambassador Edge Stack works, read the Ambassador Edge Stack Story.